Mattermost Recipe: How to use Mattermost for product vulnerability incidents¶
Problem¶
After getting access to your Mattermost instance, you’d like to set up a workflow for security incident handling using Mattermost. Visit our deployment section if you want to learn more about how to deploy your own Mattermost instance.
Solution¶
This guide walks through the set up of a product security incident room using Collaborative Playbooks and Channels with voice calling and screen sharing functionalities.
1. Workspace setup¶
For Cloud customers, all the functionalities works out-of-the-box with no technical setup. Simply invite your team members to your workspace and move onto the next section. For self-hosted deployments, refer to the calls configuration documentation to configure voice calling and screen sharing.
2. Playbooks setup¶
Now that your workspace and teammates are ready, the next step is to create a playbook for incident handling. For this recipe, we’re using an adapted playbooks template used by the Mattermost Product Security team that’s available for download here.
After downloading the template above, connect to your Mattermost workspace. Then open the product menu and select Playbooks.
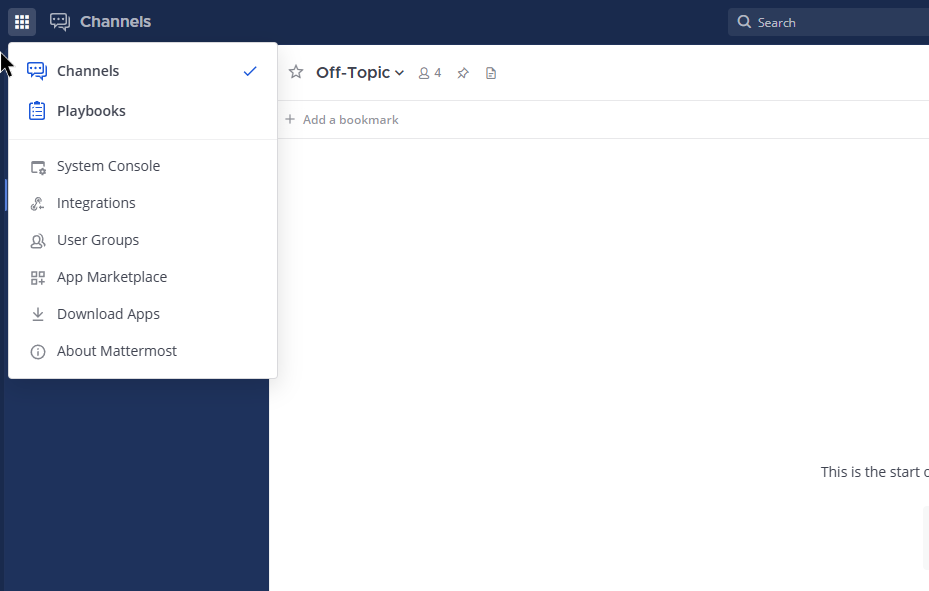
Next, open the Playbooks menu, select Import, and navigate to the file you downloaded.
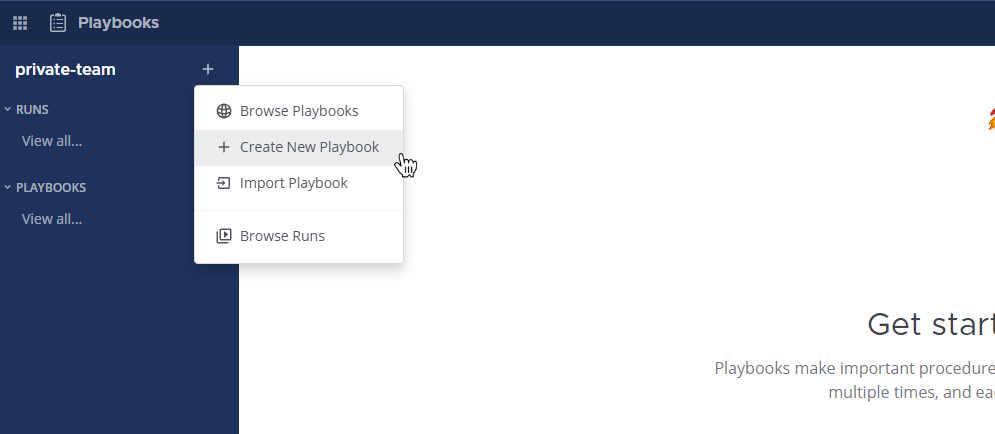
When you’ve imported the file, you should have a new playbook called Security Vulnerability Playbook. Select the three dots to edit the playbook.
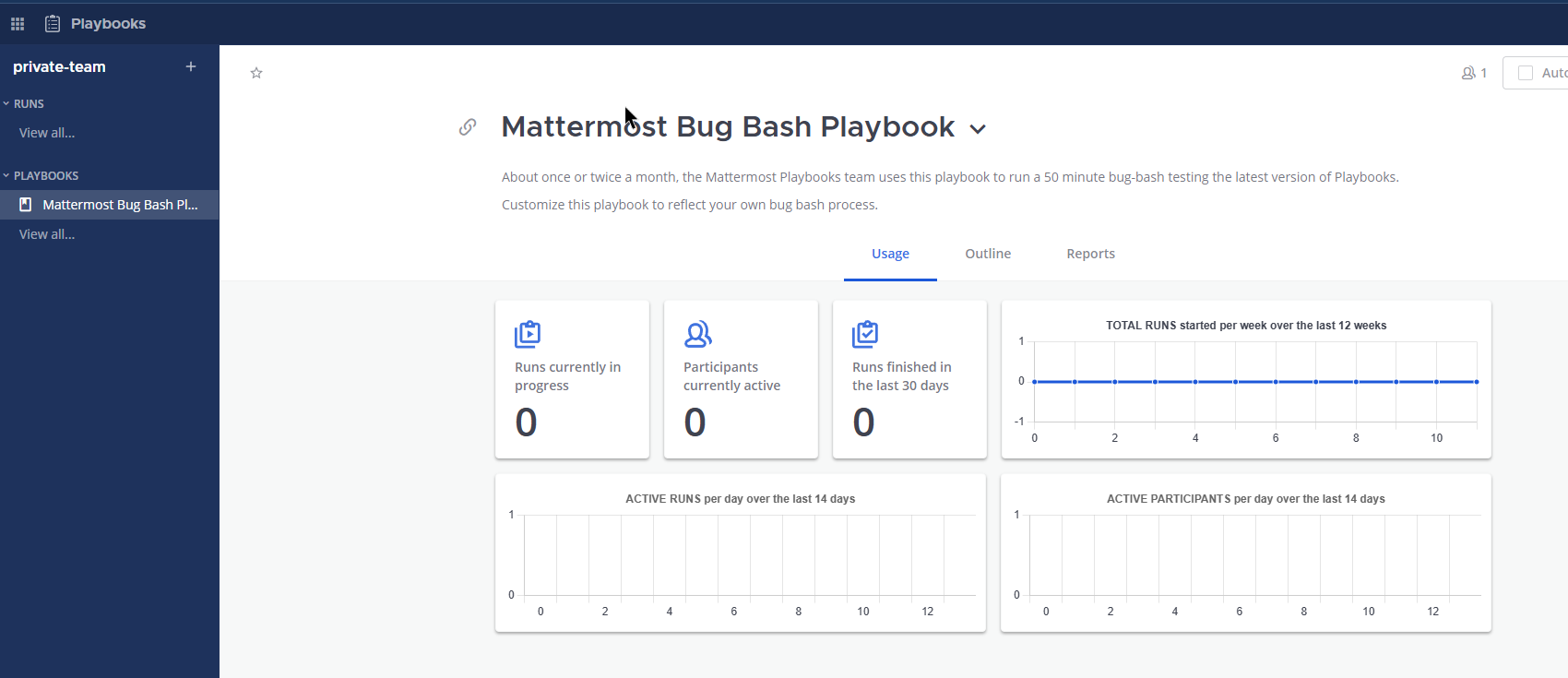
Modify any tasks or actions to suit your use case. In our scenario, we’ve assigned the playbook owner role by default to Alice and added three other team members to be automatically added in the Actions tab. We recommend changing these to the members of your security team.
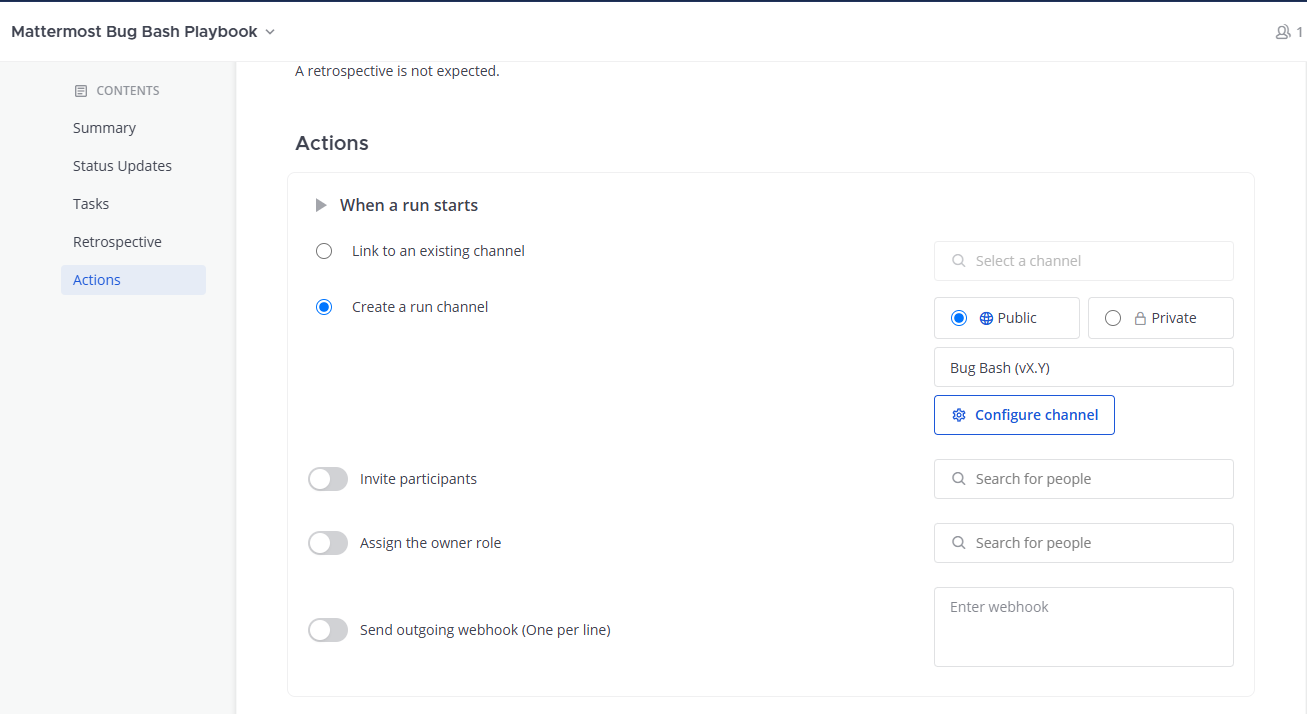
Select Save. Then, hit Run.
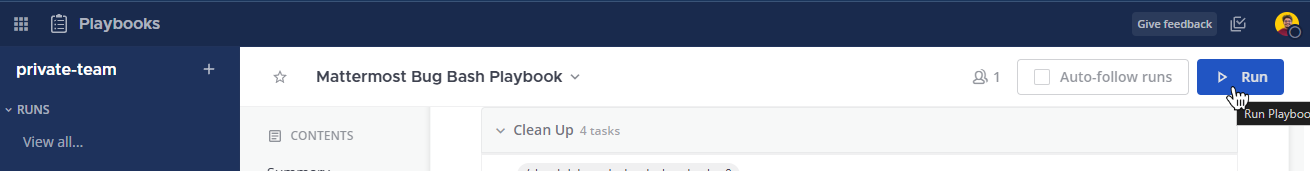
Set the title on a scenario that makes sense for your environment and select Start Run to create a new channel and invite the members as you’ve predefined.
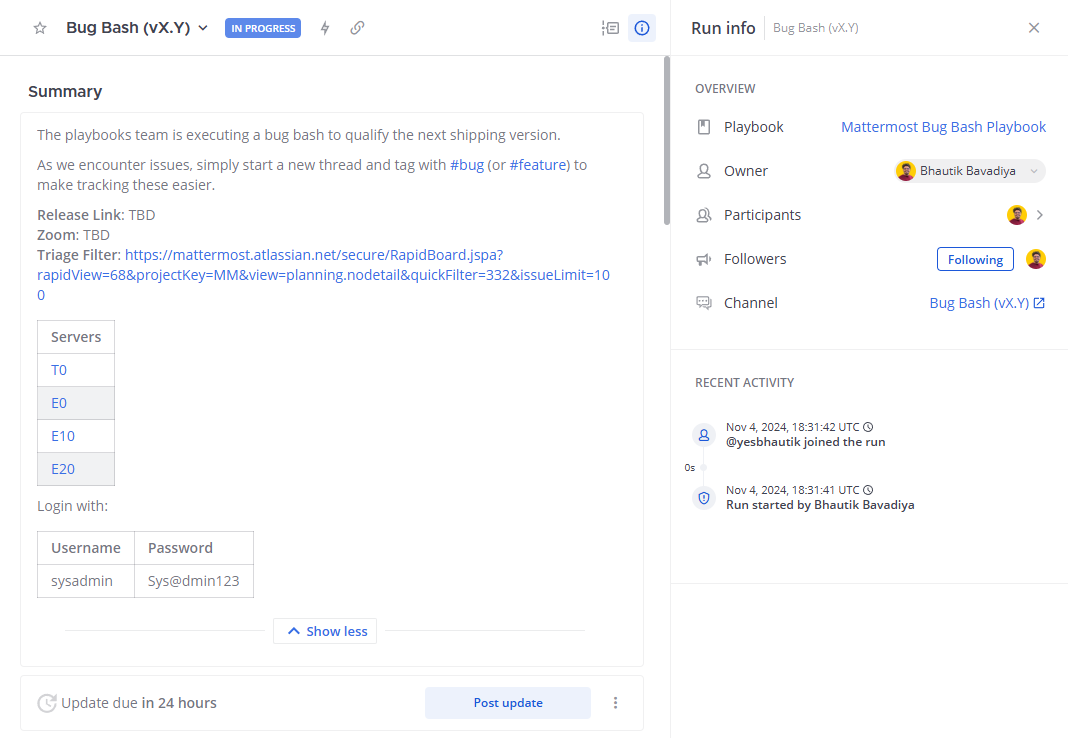
3. Using calls for voice chat and screen sharing¶
For Mattermost Enterprise and Professional customers, you can select Start call in the run channel header to kick-off a channel call. The call can only be joined by participants of the incident channel.
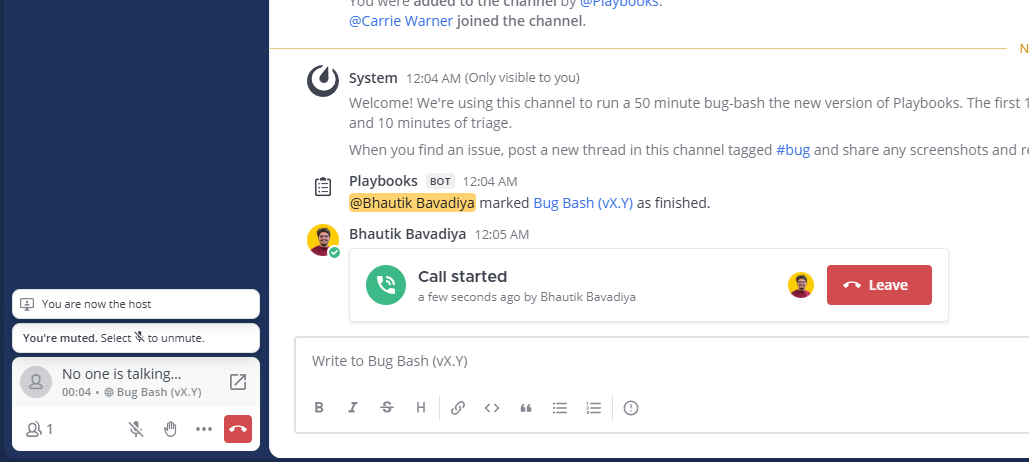
In the bottom-left corner of Mattermost, select the expand icon to open a separate pop-out window for the call, with additional options to start presenting.
For Mattermost Team Edition, only 1:1 calls are supported. Open a direct message with another incident responder and follow the same steps as above.
Note
Want to try out calls? Select Start call in the incident channel to start a free 30-day trial of Mattermost Enterprise to enable this functionality for all channels.
Discussion¶
Using collaborative playbooks you can ensure a streamlined approach to incident resolution. Our playbook template walks through a typical product vulnerability remediation aims to provide a structure resolution and also keeping the right stakeholder informed.
The playbook starts with a Triage stage that verifies the validity of the issue, continues with an Investigation of exploitation (if possible) and follows with an active Remediation of the issue. After the issue is mitigated, the incident can go into Resolution and be closed with an incident post-mortem.
When running the playbook, you can add key events, such as messages, to the timeline for easier reporting. To do so, select the app icon when hovering over a message.
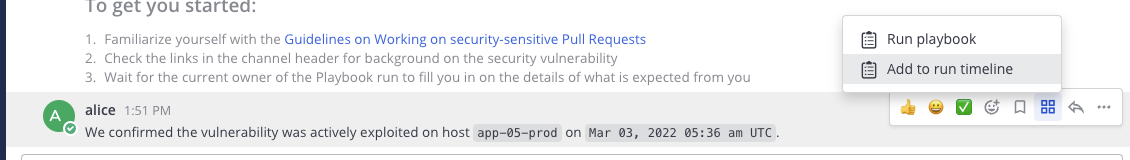
Give it a short summary that will be shown on the incident overview, with the ability to jump to the message linked.
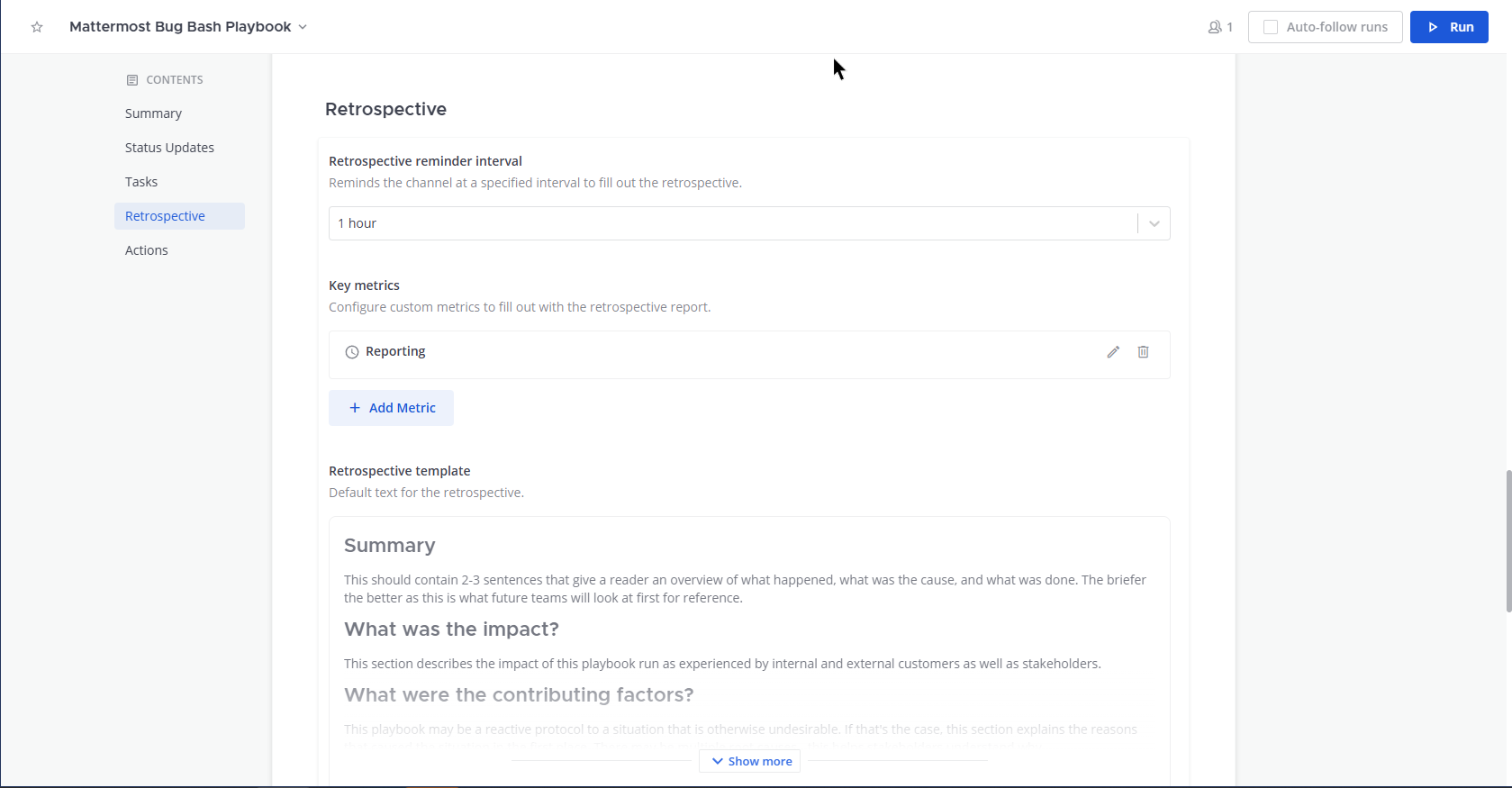
The timeline is a great feature to provide an overview of the most significant events for both active and previous events for both responders and for management.
The process and playbook shared here is only the starting point for your unique environment. By customizing the playbooks and adding additional integrations to automatically be notified about new incidents you can further accelerate your response times. Additional integrations with SIEM solutions and platforms such as HackerOne will be released in the next months.